Monolithic, multi-tiered approaches to design software has become a thing of the past in recent years. These approaches have given way to a more modular architecture, commonly referred to as “micro services.” Despite the name, some of these services aren’t actually micro at all. Isolating an app’s services into interoperable containers has revolutionized the way developers are able to update, add to, or expand parts of an app. While micro services have freed us from many of the constraints of the monolith, these benefits come with increased complexity, vulnerabilities, and risks that need to be mitigated with a tailored security strategy. It’s important to adhere to the same security standards while designing your MuleSoft integrations.
The Goal of Security Design Principles
No matter how the applications are integrated, security concerns typically reside within the network. For micro services, this gets exacerbated due to the various network connections and APIs used to forge communication channels between all those components. These create more loopholes for attach and interception of data that is in-transit. Therefore, it’s necessary to keep security design principals in mind while designing your integration using any framework, such as MuleSoft, Jitterbit or any other platform.
The goal of security design is based on:
- Digitization of Business Capabilities
- Multiple digital channels
- Confidentiality
- Integrity
- Availability
The Security Design Principles
There are seven design principles that are crucial to keep in mind when designing integration within a framework. Without these design principles in place, your data could be put at risk. The principles include networks that are:
- Standardized
- Choose the best technologies

- Targeted
- API profiling and network segmentation
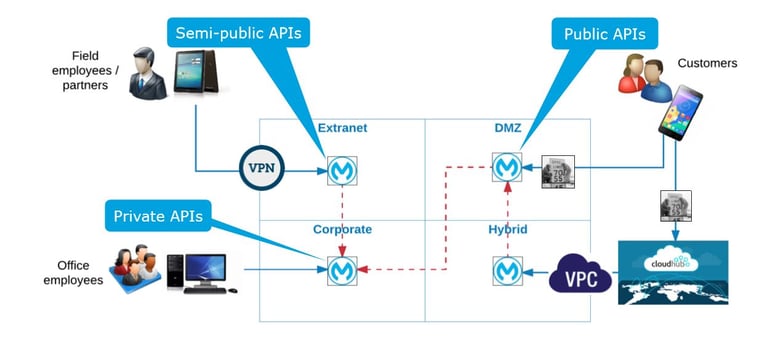
- Minimized
- Be stingy with capabilities (these include domain-driven design, business entities, and a single responsibility principle)
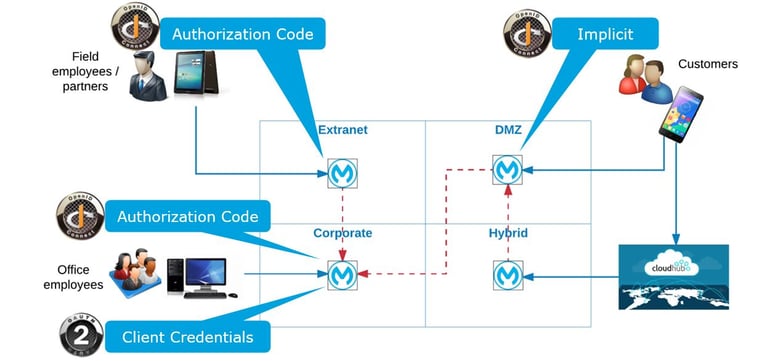
- Locked
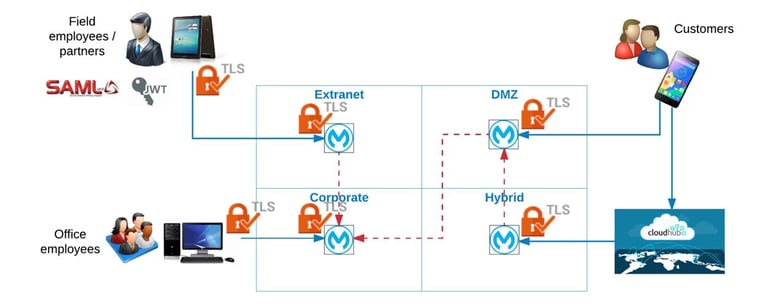
- Multi-keyed
- Use OpenID Connect and OAuth 2.0
- Use TLS, Mutual TLS, SAML, and JWT
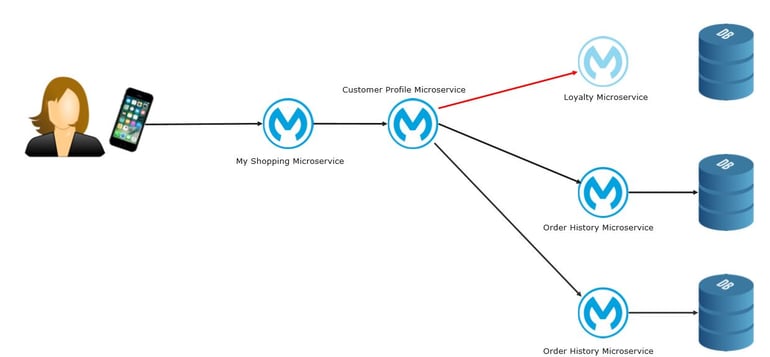
- Elastic
- Use Containerization & Container Scheduling
- Each Microservice has distinct scalability requirements
- Container scheduling makes scaling easy
- PaaS frameworks schedule containers based on traffic
- Use Containerization & Container Scheduling
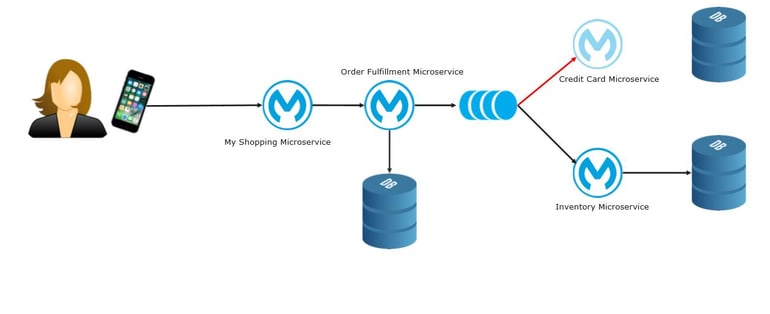
- Resilient
- Queries with the Circuit Breaker Pattern
- Commands with Domain Events
The Four Pillars of an Integration Project
The four pillars of an integration project, which are the building blocks for a solid, secure application network, are:
- Speed
- Agility
- API Security
- Innovation
Complexity can create vulnerability, and data security is a difficult enough problem without trying to extract data to fit a legacy standalone. As you design application networks, following these application design best practices can help you:
- The app emerges bottoms-up via self-service
- It provides visibility, security and governability at every API node
- Is recomposable? Does it bend, not break? Is it built for change?
Want to Learn More?
For more information about protecting your APIs, check out these related blogs:
- How Should You Secure Your API Strategy?
- Best Practices for API Development
- 5 Tips for Developing a Great API
- API-led Connectivity The Next Step in the Evolution of SOA
Or, set up a free consultation with a Mulesoft expert:
















