Biometrics is a way to authenticate a user’s digital access to systems, devices, or data using a single or combination of biometric identifiers. A biometric identifier is any physical or behavioural characteristic that can uniquely identify an individual. Fingerprints are one of the most common types of biometric authentication among enterprises, that is used by about 57% of companies according to a survey conducted by Spiceworks. Here we discuss how biometrics is revolutionizing the smartphone experience.
Benefits of Biometrics for Smartphones
- Higher Security: Biometrics provides higher security than a PIN/Password authentication. The password can be hacked and can be turned off and can also be mimicked digitally easily. Biometric identifiers, on the other hand, is much more secure and harder to simulate especially if its multi-factor biometric authentication.
- Convenience: It is far easier to authenticate using biometrics. There is no need to remember a unique and complex password. Also, you also lose productivity if in the user forgets the password. There is the additional hassle of resetting the password over time.
- Flexibility: Users can choose face ID, fingerprint ID, voice recognition or iris recognition or any combination of these to authenticate.
Different Types of Biometric Identifiers
The most common smartphone Biometric identifiers or modalities are:
- Fingerprint Scanning: Fingerprint scanning is not just for unlocking smartphones but is considered safe enough to authenticate banking, mobile payment/wallets, and other financial applications requiring high security.
- Facial Recognition: Face ID or facial recognition is the most popular way to authenticate biometrically in mobile devices. With the launch of the iPhoneX, Apple put Face ID before fingerprint scanning. Face ID in the latest iPhones, is the most secure means to authenticate purchases through Apple Pay.
- Iris scanning: Iris scanning is very similar to facial scanning. Users are required to hold the smartphone and align their eyes within the scanning frame. Currently, iris scanning is not a popular option to authenticate financial transactions.
- Voice Recognition: Even though voice recognition is not widely available as a Biometric Identifier for smartphones it is supported by some Android devices. In the future, voice recognition has huge potential as one of the leading biometric identifiers.
Here is a screen shot from Samsung Galaxy S8’s Settings app that showcases various biometric securities.
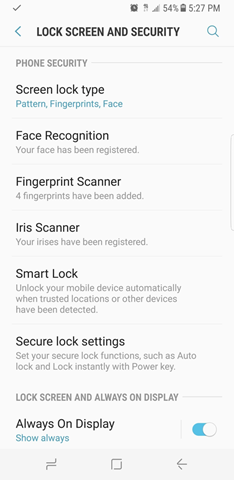
Figure: Samsung Galaxy S8’s various biometric securities Mechanisms
How Secure is Biometric Data?
Smartphones supporting biometric authentication comes with a hardware security module where all information pertaining to the user’s biometric data like fingerprint scan, facial image, voice print is safely stored. During the authentication process, biometric information is collected by the fingerprint reader, camera, or microphone and sent to the module. This module compares the information received from the hardware to original data stored by the user and if matched successfully, permits access. This ensures that the original biometric data of the user is never shared with any software or system outside the module, including the phone's operating system. In iOS, this module is called the “Secure Enclave” and in Android, it is called "Trusted Execution Environment.”
Architectures for Implementing Biometrics
Biometric authentication for mobile apps can be implemented with two architectures:
1. Server Centric Architecture
In this architecture, biometric data is stored centrally in a secured server. During authorization, the captured biometric sample is sent to the server, where it is processed and mapped against the stored biometric data.
Advantages of Server-Centric Architecture
- Central control of the authentication process
- Analysis of data to improve matching and detection performance
- Works well even for Mobile devices with less computing capacities
- A user can register a biometric identifier from one device, and login from another device, providing a SaaS experience
- Authentication details are secure, even if the device is stolen or misplaced
Device Centric Architecture
In this architecture, biometric data is captured, stored, and matched with sample data from sensors, all on the local device.
Advantages of Device-Centric Architecture
- Prevents large-scale breach in case of a server hack
- High scalability due to independence from the server
- Secure even in case of a man-in-the-middle attack
Both architectures have their fair share of advantages. Architecture can be chosen based on business requirements.
In short, biometrics is revolutionizing the way authentication is achieved, especially in mobile devices. It is still in its early stages, but considering the scale of some cyberattacks, ensuring security with biometrics is becoming a top priority.
 About Author
About Author
Sreeraj P R works as Sr. Software Engineer at V-Soft Digital and has over 6 years of experience in the IT industry. He has profound expertise in Mobile Application development for Android and iOS using Xamarin. He also has experience in web technologies like ASP.Net.

.jpg?width=1110&name=Fingerprint%20scanning%20(1).jpg)













