With increasing cybercrime losses, enterprises are investing massively in their cybersecurity infrastructure; which is projected to be $1 Trillion by 2021. Despite all these efforts, cyber attackers are taking intelligent ways to launch the attack, where many attacks went unnoticed for months. The proactive approach of enterprises to counter these attacks resulted in the evolution of Cyber Threat Intelligence (CTI). Here we give a detailed analysis of what Cyber Threat intelligence is and how it is going to make your organization assets secure.
What is Cyber Threat Intelligence?
So, prior to understanding what cyber threat intelligence is It is necessary to understand the basic difference between threat and risk. Though both appear to be similar, they have different implications and handling them takes altogether a different approach.
Understanding Threat Vs Risk
The threat is a possibility or competence of the attack intending to cause probable damage to organizational assets. The persons who launch threat attacks are called threat actors. Threats exploit the vulnerabilities to conduct the attack on the organizational assets. Threats can be due to human (hackers) involvement or any natural mishaps (floods, electrical issues, and so on).
The risk is probable damage or loss that results due to a cyber attack. David Strachan Morris, Pilgrims Group Limited, defines risk as the function of the probability that your organization will be involved in an attack and the harm that such an attack would cause.
Defining Cyber Threat intelligence
Gartner defines Threat intelligence as, the evidence-based knowledge, including context, mechanisms, indicators, implications and action-oriented advice about an existing or emerging menace or hazard to assets.
Threat intelligence will enable organizations to be proactive and predict vulnerabilities that may be exploited by the attacker. Threat intelligence tools should scan over all the business systems on regular basis to check the vulnerabilities or affected parts of the systems that are to be fixed. Performing cybersecurity threat analysis requires a deeper understanding of diverse network security threats and its patterns, impact and how to avoid them. This entire process is called Cyber Threat Intelligence.
Essentials of Formulating Cyber Threat Intelligence
Most of the organizations conducting cyber threat Intelligence do involve either their internal teams or some external vendors. Irrespective of who conduct this process, the key sources through which CTI process data is extracted are:
- Intrusion Detection System reports
- Firewall
- Endpoints
- Vulnerability assessment data
- Access and user account information
- User behavior analysis
- Honeypots
- Data from third-party administrators
- Network telescopes
- Reputed Security research groups (like CERT, CISO)
- Regulatory agency information
- Open Source public groups/forums
How does Cyber Threat Intelligence (CTI) help your business?
It is observed by the SANS research that more than 42% of organizations participated in their survey have dedicated to the team for CTI. Following are the ways getting a right CTI can enable your businesses to stay fit against cybersecurity threats:
- Improving visibility into threats and attack methodologies impacting our environment
- Refine security processes to stay in tune with the cybersecurity trends
- Trace out the list of procedures and sources that are
- Detecting unknown threats
- Better threat management
- Picks up the vulnerabilities in the systems that are to be exploited by the attackers
- Better scope to handle cybersecurity risks
- Brings down the time to detect and counter the security incidents
- Proactively predict and counter security breaches
- Keeps your organization’s cybersecurity team to be ever ready to protect against hackers
- Reduces the impact on the organization’s systems or data losses.
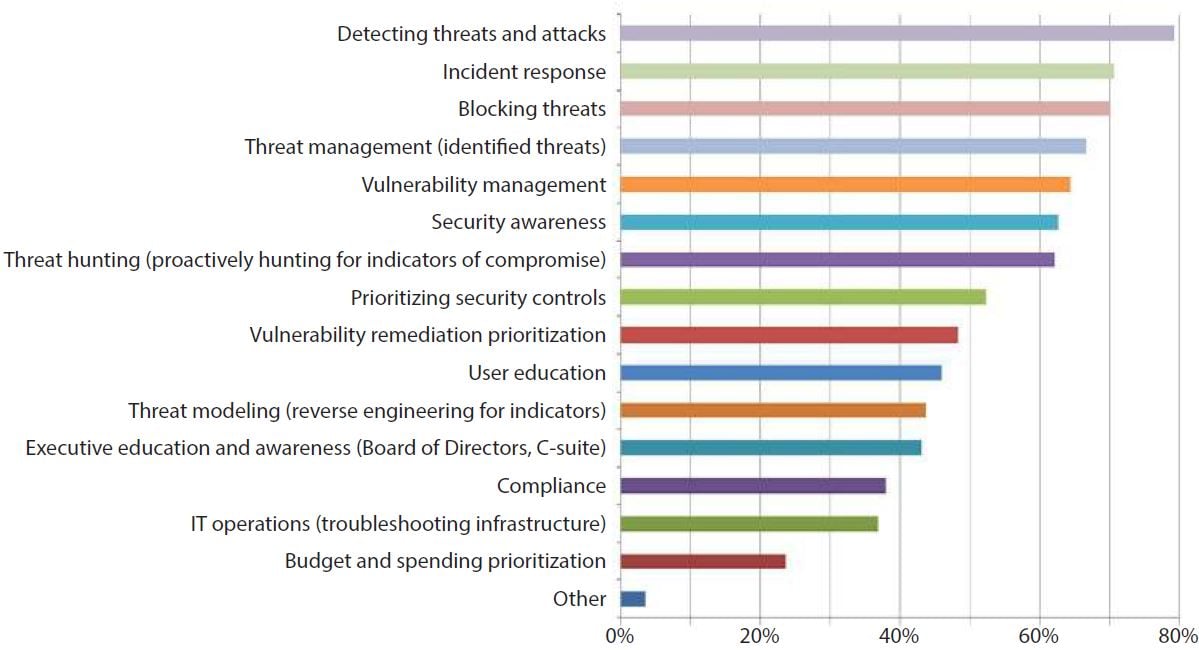
Apart from the above benefits CTI has, here we bring some other insights from the SANS Survey on Cyber Threat Intelligence in Security Operations:

.jpg?width=1110&name=Secret_Service_Electronic_Crimes_Task_Force_(ECTF).jpg)













