The world now is at the pinnacle of the smart phone revolution, where each and every service you need can be accessed with the smart phone in your pocket – be it banking, shopping, health care, education and more. As these app-based services become more prevalent and widely used, the number of people looking to exploit and abuse you and your business is growing bigger.
So what are the different ways in which mobile apps get hacked? See the illustration for an overview, and review the detailed descriptions of each method below the diagram:
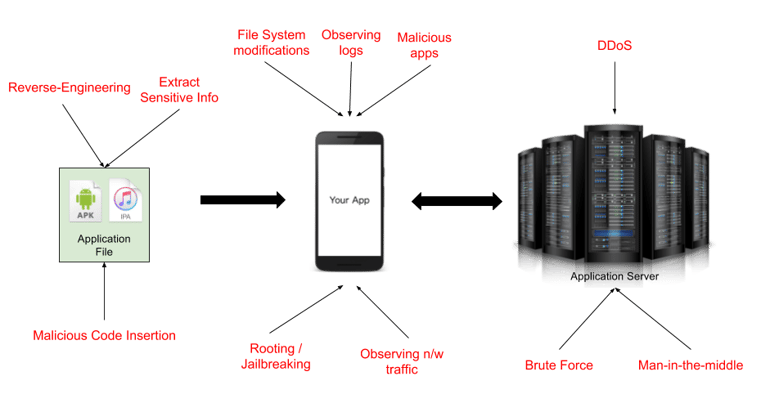
Application Binary-Level Attacks
Unlike web apps, mobile apps are able to be exposed to binary-level attacks, as this application must be made public. The attacker is capable of downloading the app and compromising the source code and exploiting it. Ways of doing so are:
Reverse-engineering
Some hackers use dedicated tools to reverse-engineer the app's source code. This can reveal a company's core business logic, which can be used by competitors to steal ideas and tactics.
Extracting sensitive information
Some tools are available which can extract string constants from the binary. This can call out critical information, such as an Administrator's login credentials, or a sensitive URL.
Inserting malicious code and redistributing your app
Some hackers will hack directly into the binary file of the app, then insert their own malicious code into the binary itself. They will then distribute the app through unofficial channels and gets them installed on the unsuspecting user's devices.
Doing so enables them to do things like 'phish' a user's details, redirect users to their website/products unwittingly, or show things that can harm your company's reputation and credibility.
Mobile Device-Level Attacks
A device-level attack is when a vulnerable device is exploited to gain access to a network. The attack can be performed on any connected device(s). They come in many different forms, such as:
Malicious apps that steal data
Hackers distribute their own apps disguised as games, utilities, etc. which will, behind the scenes, observe user’s actions and inputs. Thus they'll be able to steal lot of details such as, what other apps are installed, all of the user's keyboard inputs, all network activity, etc.
Installing your app on Rooted / Jail-broken devices
Hackers modify the OS installed on their phone and then run your app. With this, they are able to observe the internal activity of your app like what data you are storing internally, what network calls are being made, etc., which a normal user would not be able to see. With all these data available, they have more knowledge about how your product or service is working, and can abuse them.
Modifying app data
Hackers will look at the file system and see how the app is storing files and data locally. Sometimes modifying the data files can make the app behave differently to suit the hacker's intents. For example, by modifying a file, the hacker might be able to appear logged in to the application, without any credentials.
Observing logs
Sometimes the developers of the app put logs to debug the application, and forget to remove them before releasing to production. Anyone can simply observe these logs and get insight into the working of the apps.
Observing unencrypted network traffic
If the app's communication with server is not encrypted correctly, all the communication can be read in plain language by an observer. This includes the credentials passed to the server, sensitive information returned by the server etc.
Server-Level Attacks
By hacking the mobile application as described in the previous two levels, the hacker could have gained knowledge about how the app is interacting with the web service, and can try to exploit the web service.
- Man-in-the-middle attacks: The hacker understands the API calls made by the app, and uses authentication sent by the app and poses as a legitimate user. The unsuspecting server might serve confidential data to the hacker.
- DDoS attacks: By knowing the API end points used by the app, the hacker could use automated tools to push heavy traffic to those end points, causing the server to go down. In effect, your product or service would become unusable to real users.
How to Keep Your App Safe
To make sure your app holds out against these attacks and to provide the best security to your products and users, the Mobile Practice team at V-Soft Consulting Business Solutions have certain standards and best practices, which are followed right from writing the first line of code. These are on top of standard measures like never putting any sensitive information in the code, disabling all logs on production builds, cleaning up all user inputs before processing them, adding Crash Reporting and Analytics to detect any unusual app behaviour etc.
- Never store credentials on the device: Never store any sensitive information like username and password on the device, even in the app's private space. Instead, use OAuth or other token-based authentication to make requests on behalf of the user. Also, ideally refresh and expire user sessions after a pre-set amount of time, to prevent any compromised authentication info being misused for a long time.
- Use app's private space, and use encryption for storing any user data: In all operating systems, there is a dedicated space for each app to store its data, which is not accessible to regular users. To prevent even a user with root access from reading this data, encrypt all data in this region as well. Never use public data region like an SD Card to store any app's data.
- Keep your app and its components up to date: Each day, hundreds of vulnerabilities are found in the mobile and web space and patches are released regularly. Developers should make sure that they incorporate these patches in their applications and encourage their users to update their app regularly. This will ensure that hackers who attempt these known vulnerabilities will be unsuccessful.
- Use obfuscation on production builds: To thwart efforts to reverse-engineer the app binary to extract core business logic and other sensitive information in the code, use obfuscation--intentional obscuring of data--and minifying. This will not only make the reverse-engineered code hard to read, but will also make the app binary more compact in size. Proguard is an example, available for Android.
- Use HTTPS for all API communication: HTTPS is a secure protocol for encrypted communication in an open network. When using HTTPS, a person who is observing the network activity will not be able to get any information about the requests, such as the URL, login/authentication information, or any of the data passed through the web service.
Over and above these, depending on the high-security requirements of the client, we also include the following features to prevent and contain any security issues:
- Built-in ability to clear app data remotely: If we come to know that a device has been compromised or login credentials have been hacked, we will provide a remote web dashboard giving you the capability to easily change the login credentials or perform a data wipe of the device through an API or even a simple SMS.
- Detect Rooted/Jailbroken devices: The app will be built with the capability to detect whether or not it is running on a compromised device and can intentionally stop itself from running.
- Detect a tampered app binary: The app can be built with the capability to check whether its binary has been modified by inserting or removing some part of its code by verifying its files' Checksum. Once detected, it will proactively cease operation to prevent further damage.
Trusted Mobile App Development
Products and Services these days have a requirement of deeply interacting with its users. They also cannot compromise on the ease-of-use of these products. These two factors open up a lot of security issues.
Even though no system can be 100% secure, V-Soft Consulting firmly believes that with our experience developing secure applications and an experienced team that keeps track of and adopts all latest developments in mobile and web space, we can build apps that can stand strong against attacks and represent your business value proposition.
If you are interested in having a safe and secure mobile app developed for your business, register for a free 30-minute consultation with one of our mobile app development experts today.















