Cybersecurity continues to challenge businesses in their digital transformation journey. Businesses distributed across different locations and hybrid workplace environments demand a stringent security operations framework across the organization. Gartner information security research reveals that the “global information security market is forecasted to reach $170.4 billion in 2022.” Establishing a full-stack security framework is challenging and costly not only to small and medium businesses, even for large-scale enterprises too. ServiceNow offers full-stack Security Operations (SecOps) for businesses to handle security tasks efficiently and proactively.
Capabilities of ServiceNow Security Operations
ServiceNow Security Operations is a security orchestration, automation, and response (SOAR) engine built on the Now Platform. It is intended to assist security and IT teams to react more rapidly and effectively in handling security incidents.
Incident Response Management
Businesses use various security tools to handle risks proactively and ensure robust security. The ServiceNow Incident Response Management module offers simple integrations with third-party security tools and processes, coordinates with these tools to detect, classify, and make resolutions to security incidents. Based on the incident reports, alerts are fed by the security information and event management platform to avoid risk occurrence. Businesses can configure IT infrastructure to handle security incidents in an organized way.
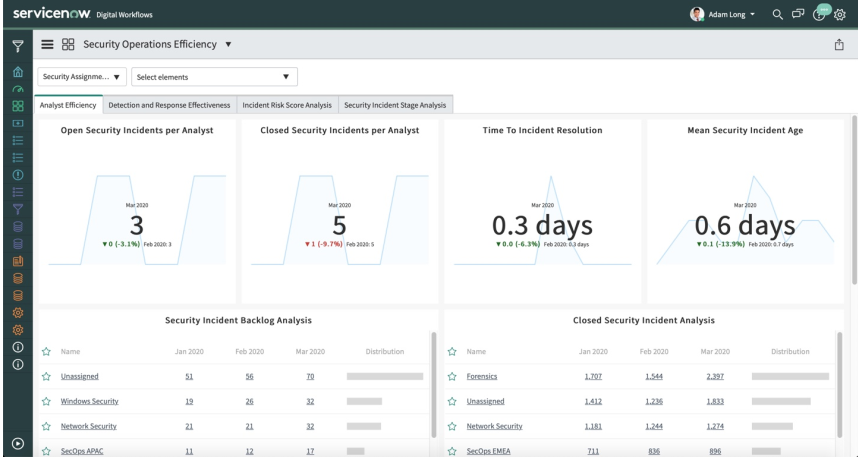
The ServiceNow Incident Response dashboard creates a consolidated view of security performance activities, where IT teams can recognize and distinguish various security trends to assess and evaluate various blockades to security. The entire incident response management is fully automated and uses ServiceNow Predictive Intelligence to identify, prioritize, and monitor the impact of security incidents. This accelerates the issue resolution time. Being a scoped application model, ServiceNow SecOps provides secured access to only specific information. The IT teams can immediately connect with the appropriate team to handle an incident.
Figure: ServiceNow Security Operations Efficiency dashboard
Vulnerability Management
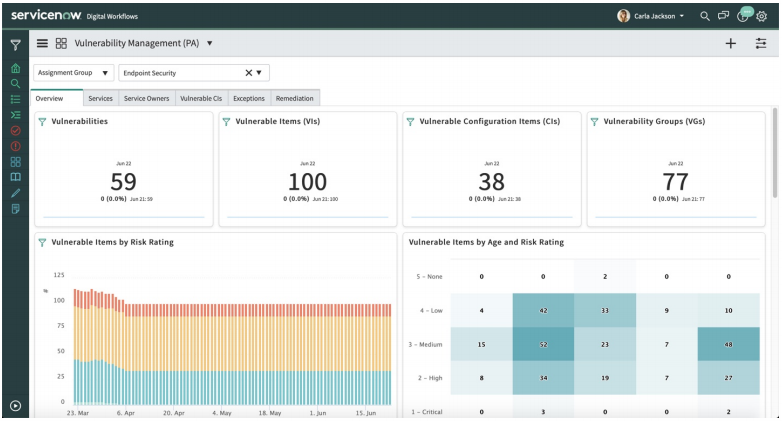
The ServiceNow Vulnerability Response application traces, prioritizes, and solves vulnerabilities in the organization. Using ServiceNow PA capabilities, the vulnerability response application gathers and analyses data that indicates the possibility of risk, identifies the vulnerabilities, and recommends the areas of progress. By integrating with ServiceNow CMDB, the vulnerability response dashboards provide an in-depth view of all vulnerabilities of a selected IT asset or business service and show how the vulnerability could impact the overall organization. Based on the impact study, the vulnerabilities are prioritized and respective solutions are implemented proactively. The IT team can also monitor the progress of the solution implementation.
ServiceNow permits IT teams to initiate workflows where the vulnerability scan data is imported into the vulnerability response application with APIs. These reports are tallied with CMDB and the assets at risk are designated a risk score. The risk score parameters can include multiple factors that can be defined based on the organization’s security policies. When crucial vulnerabilities are uncovered, this application automatically prompts an emergency response workflow that alerts stakeholders and raises a request to the IT team to react. Without having to manually detect the risk and designate responses, the automated workflows can extract the data and responses from the National Vulnerability Database (NVD).
Based on the real-time risk assessment data, the risk scores are updated, and priorities are adjusted accordingly. These stand as a guidepost for the security policy to stay updated. In compliance with the security policies, IT teams can run checks to uncover misconfigured applications and fix them.
Figure: The Vulnerability Response dashboard lists out active vulnerabilities
Threat Intelligence
Even though businesses invest heavily in security infrastructure, there are still a lot of security mishaps. This is due to the lack of detailed visibility into IT infrastructure, applications, and services. Moreover, cyber-attacks are using advanced technologies like AI and machine learning to launch attacks. It is challenging for businesses to have an intelligent approach to handle these threats. For this reason, IT and security teams are unable to precisely locate the reasons behind most vulnerabilities and IT teams are failing to prioritize vulnerabilities and respond to the incidents accurately. This is where the ServiceNow threat intelligence capabilities make a huge impact in improving security operations.
The Threat Intelligence application reads data and offers a point of reference to the Structured Threat Information Expression data. Using advanced capabilities of AI, threat intelligence proactively predicts vulnerabilities that an attack may focus on. This application constantly scans the applications, services, and other specific business processes to check vulnerabilities that should be fixed. As part of threat intelligence, one can list out the sources that should be constantly monitored. To run threat intelligence, ServiceNow uses Structured Threat Information Expression (STIX) and Trusted Automated Exchange of Indicator Information (TAXII) technologies, where STIX is a standardized approach to represent cyber threat information and TAXII enables easy exchange of threat information.
Performance Analytics
Organizations should discover, prioritize, and resolve threats before a risk or threat occurs. But incompetent labor-intensive procedures are widening the gap between security and IT teams to collaboratively function to detect and respond to risks quickly. The is due to a lack of real-time visibility into the overall security infrastructure and operations data. This is what the ServiceNow security operations module solves by integrating with the ServiceNow Performance Analytics.
This application provides dashboards to report, evaluate, and monitor the performance and effectiveness of security operations based on the key performance indicators that are specific to business needs. ServiceNow PA dashboards facilitate IT teams to monitor various security trends and performance to identify areas of improvement.